# Permission System
- This system adopts the typical
RBAC0 model, which implements permission control throughUser-Role-Permission (Menu Permission + Button Permission)
# Application Management
The
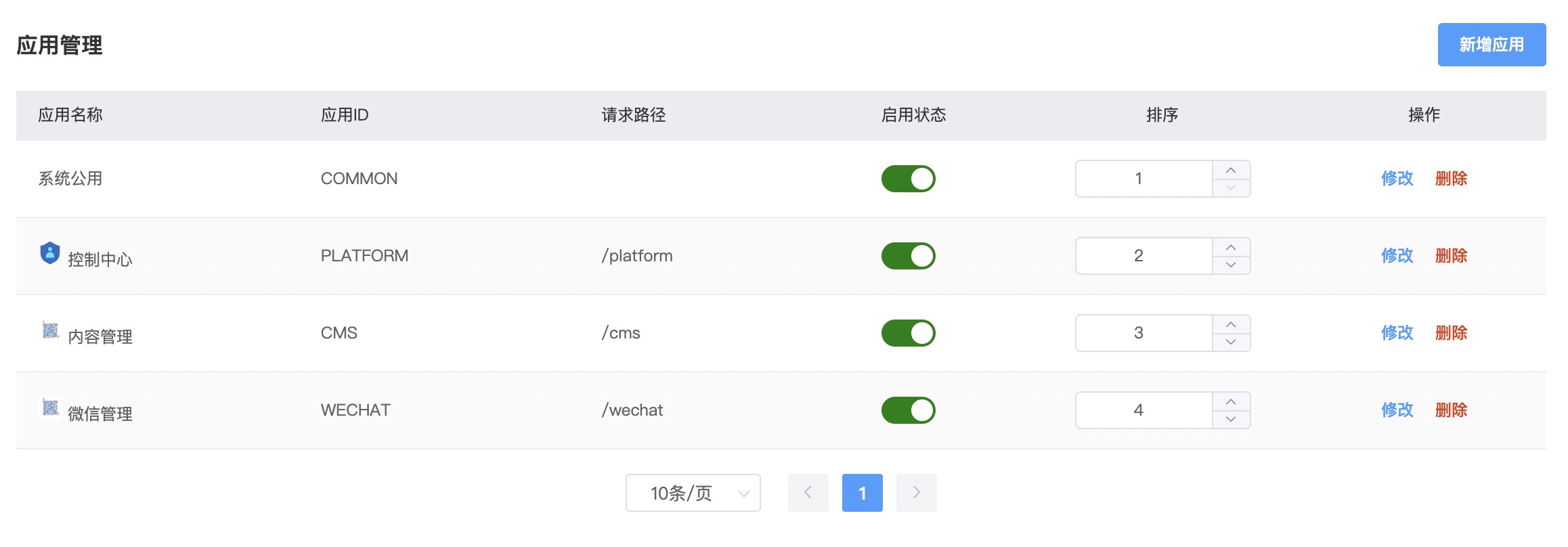
API Gatewaywill route proxy through the application'srequest path. You can divide the system into different applications according to business characteristics, and configure menus and permissions for each application separatelySystem Common [COMMON]is for system common content, such as configuring common system parameters, common menus for all applications such as internal messages, modifying personal information, changing personal passwords, etc.Control Center [PLATFORM]is the system's basic application, providing business implementation of the user permission system, management functions for basic business tables, etc.User Center [UCENTER]is a built-in application that does not need to be created, mainly providing functions such as user login, verification code, third-party login, etc.
# Menu Management
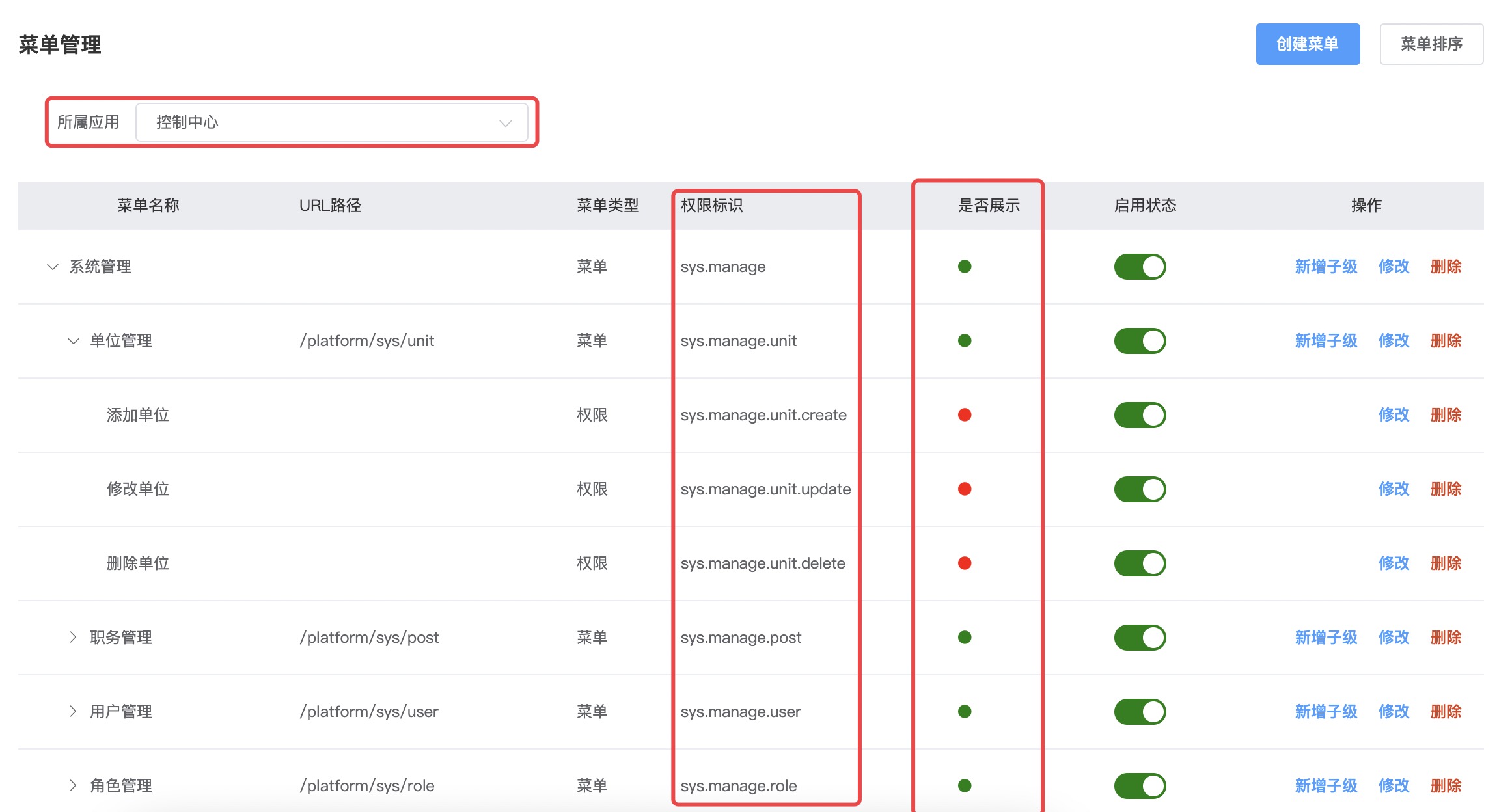
First-level menus are function categories, second-level menus are specific functions that need to configure URL request paths, and third-level menus are internal page jump paths (if interaction can be implemented with pop-up boxes, try to avoid jumps)
The
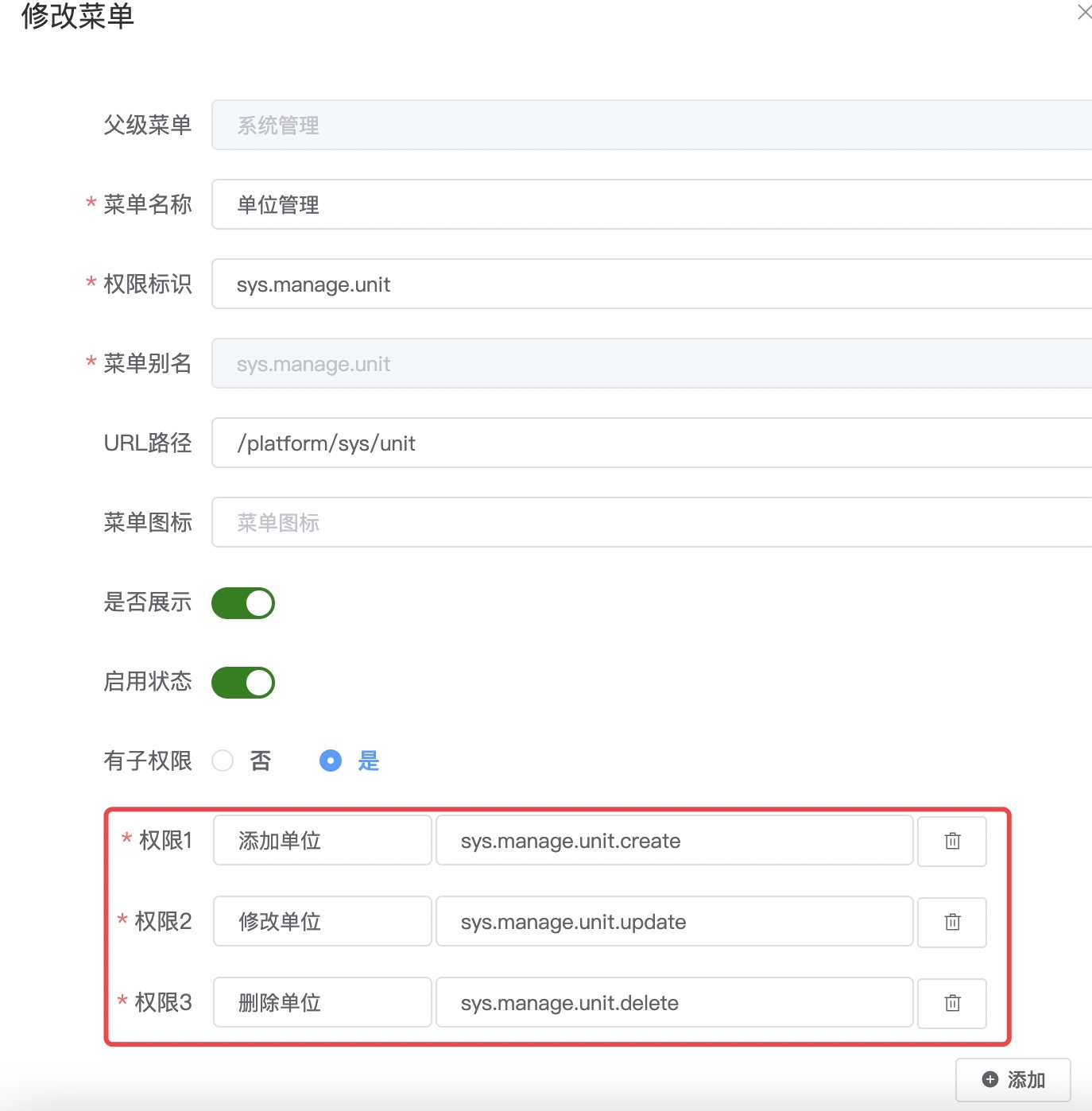
Displayattribute determines whether the configured menu is displayed in the frontend navigation barMenus need to set a globally unique
Permission Identifier, and menu sub-permissions also need to set aPermission Identifier. In the framework, the permissions owned by aroleare a collection ofPermission Identifiers
# Organization Management
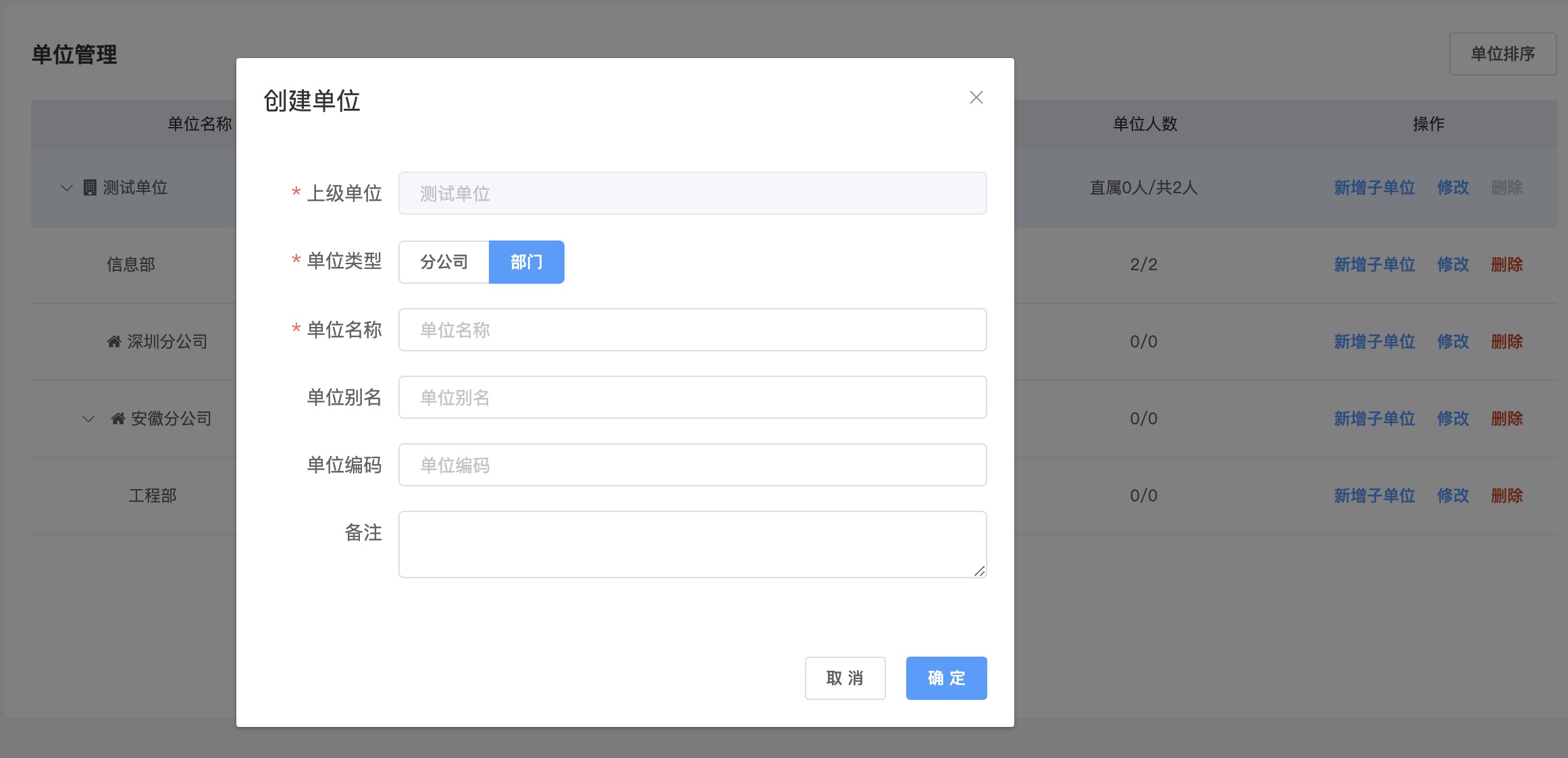
The top-level organization is
Headquarters (or Company). UnderHeadquarters, you can createBranch CompaniesorDepartments.Branch Companiescan only createDepartmentsDuring business development, business tables can store both
unitIdandunitPathfields.unitPathis thepathfield of the tree-structured organization table, with a maximum length of 100, 4 digits per level, such as a string like00010001. You can quickly query parent-child relationship data through thelikequery statement
# User Management
Usersmust belong to a certainOrganization. When creating a new user, you need to select the organization on the left first
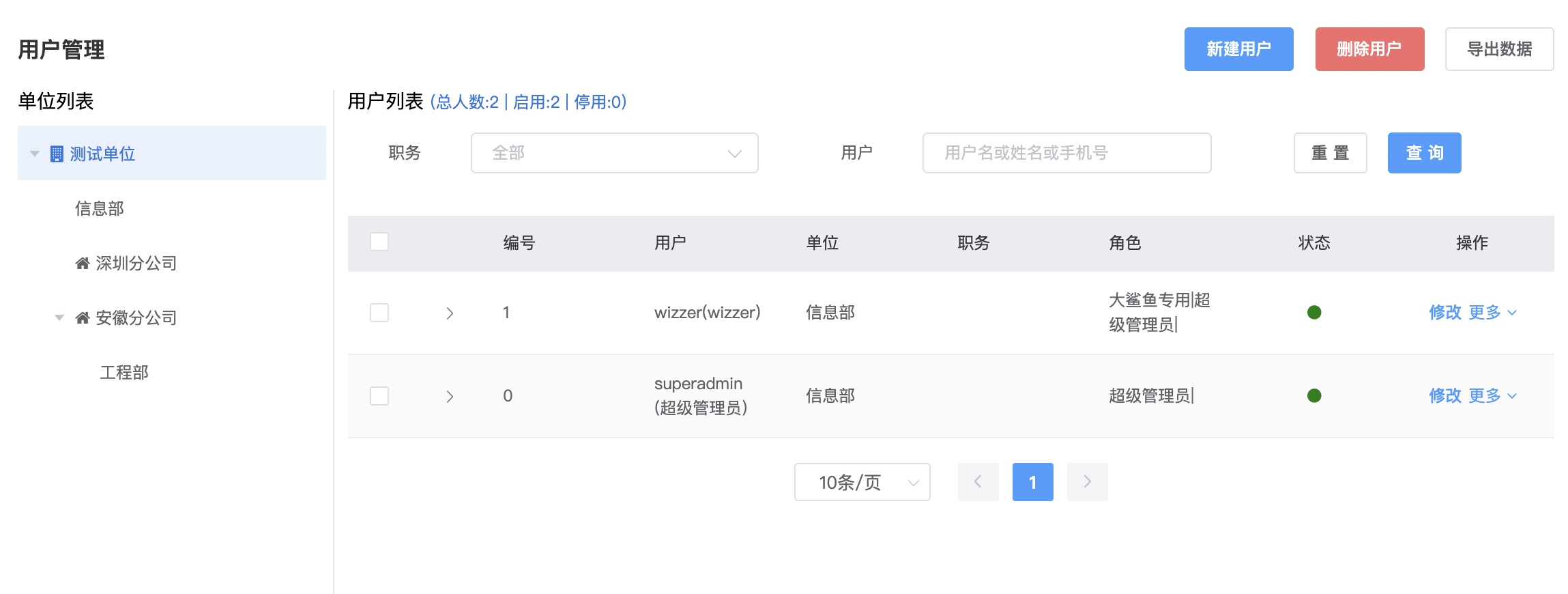
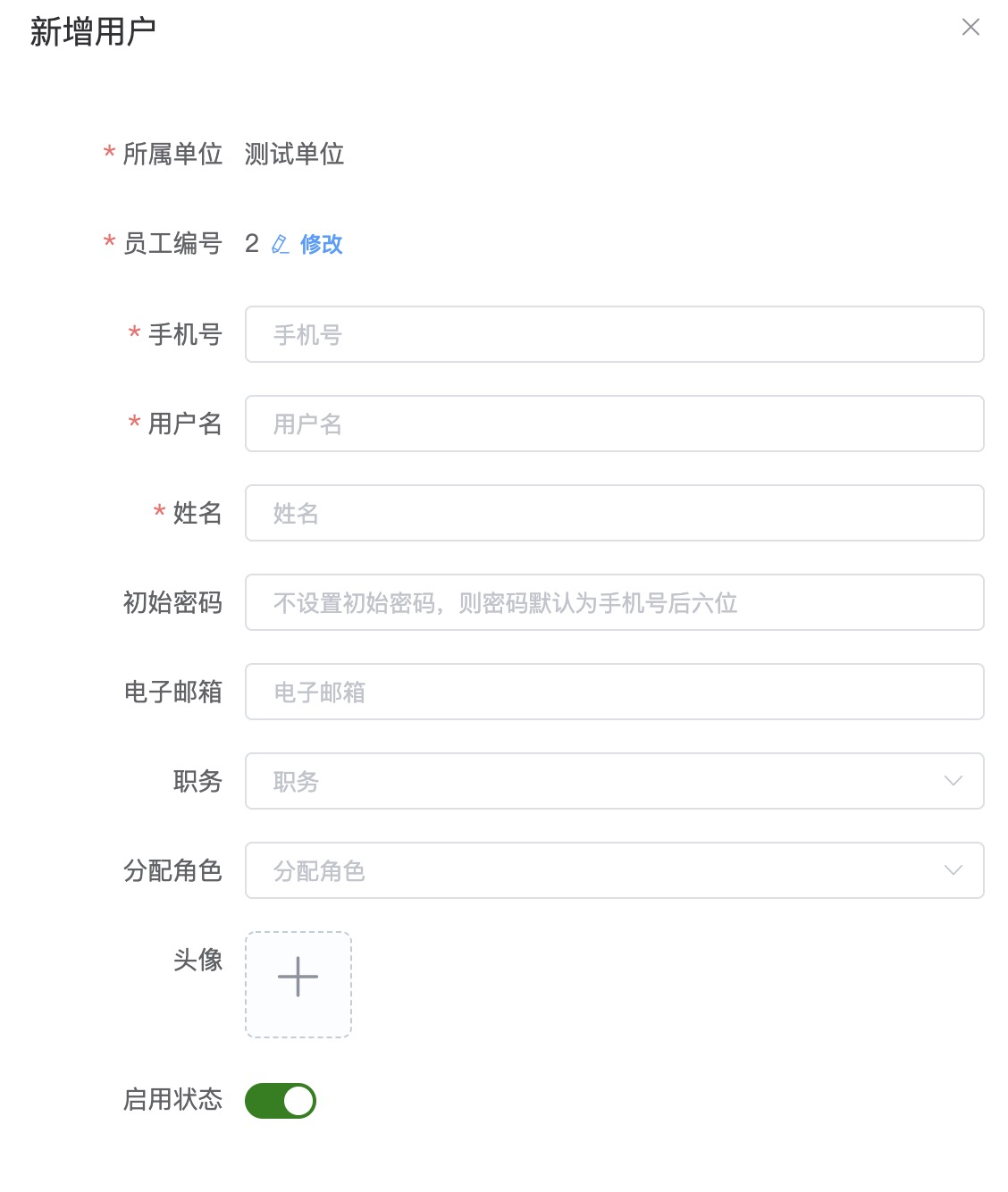
It is now quite common for mobile phone numbers to be the same as usernames. The system defaults to using the last six digits of the mobile phone number as the login password
In V7/V8, you can set whether users need to forcibly change the default password when logging in through
Account Security SettingsMultiple roles can be assigned to a user, such as system common roles, company or branch company roles
# Role Management
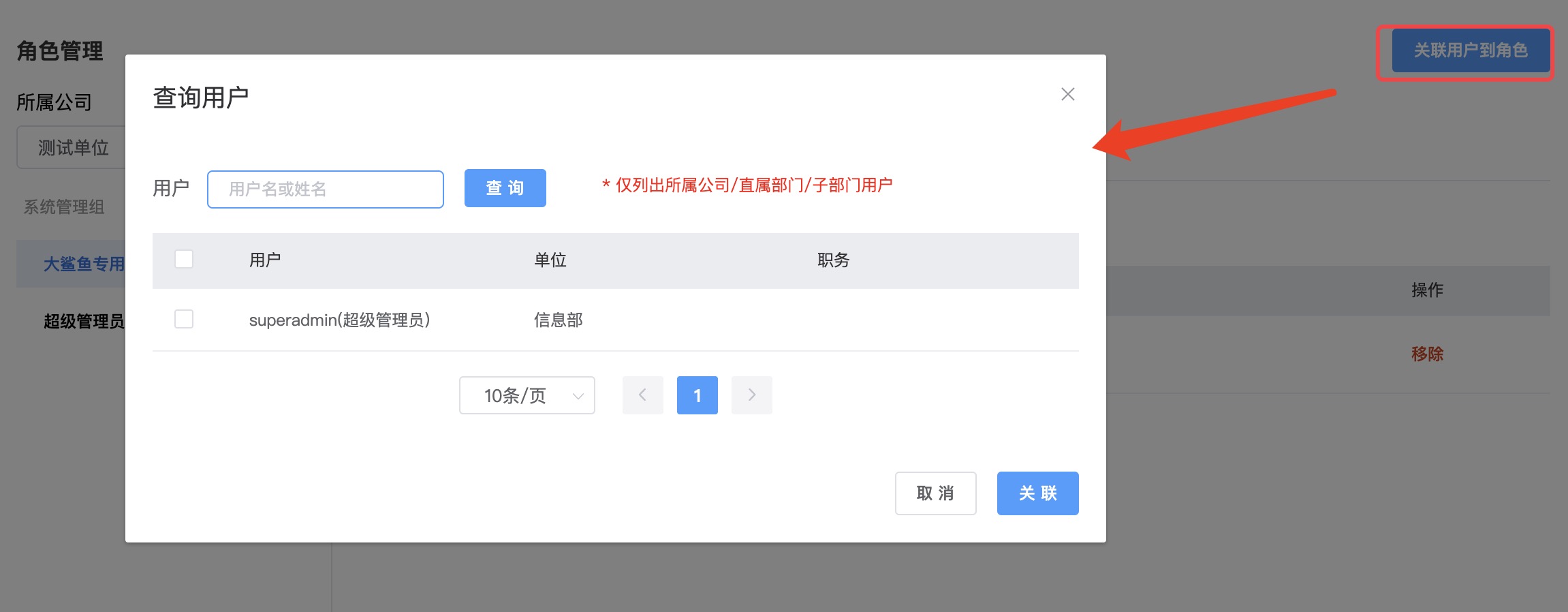
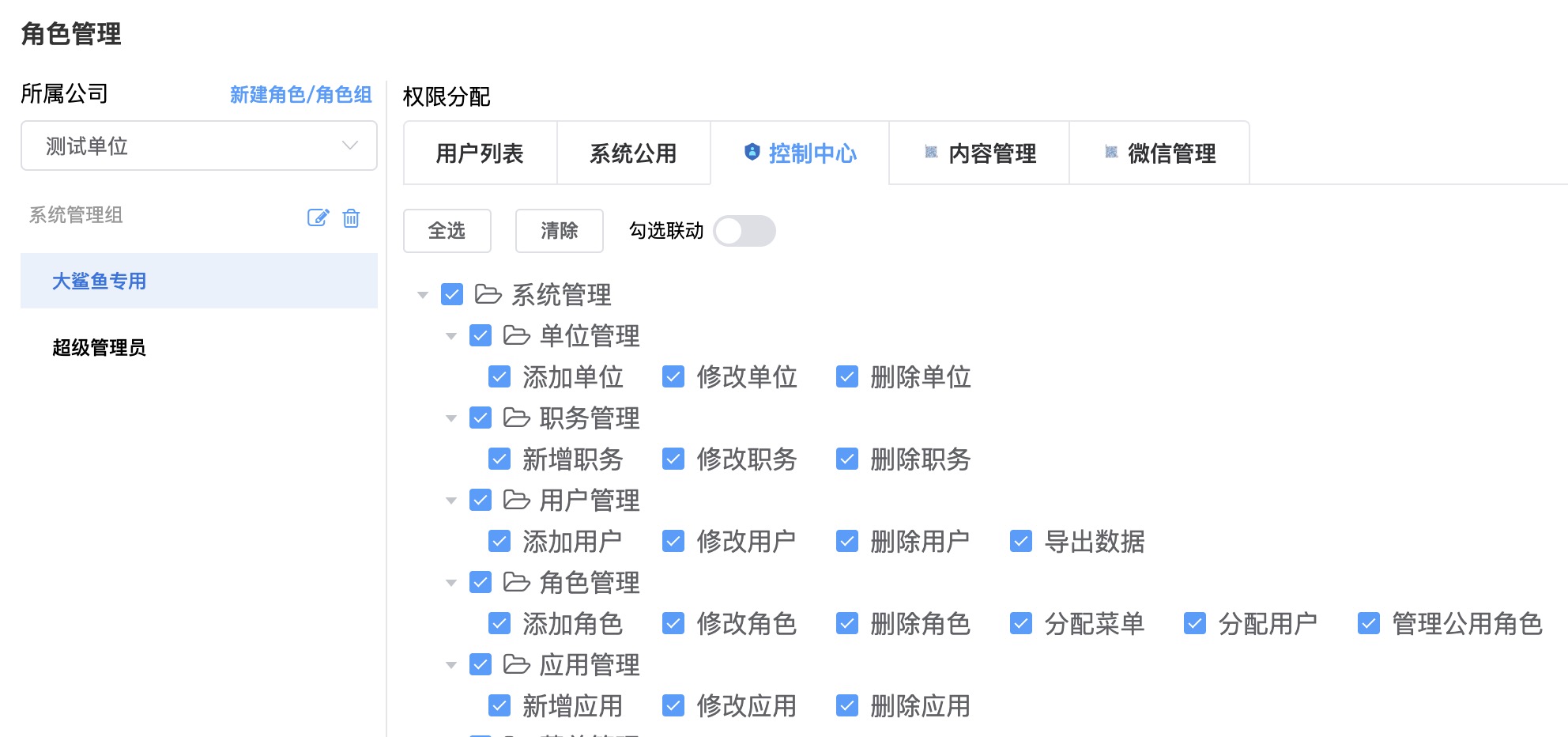
Select
Headquarters or Companyon the left, select aRole, and on the right, you can view theUser ListandMenus and Permissionsfor each applicationSystem Common Group-Common Roleis a system built-in role. TheMenus and Permissionsassigned to this role are owned by all users by default
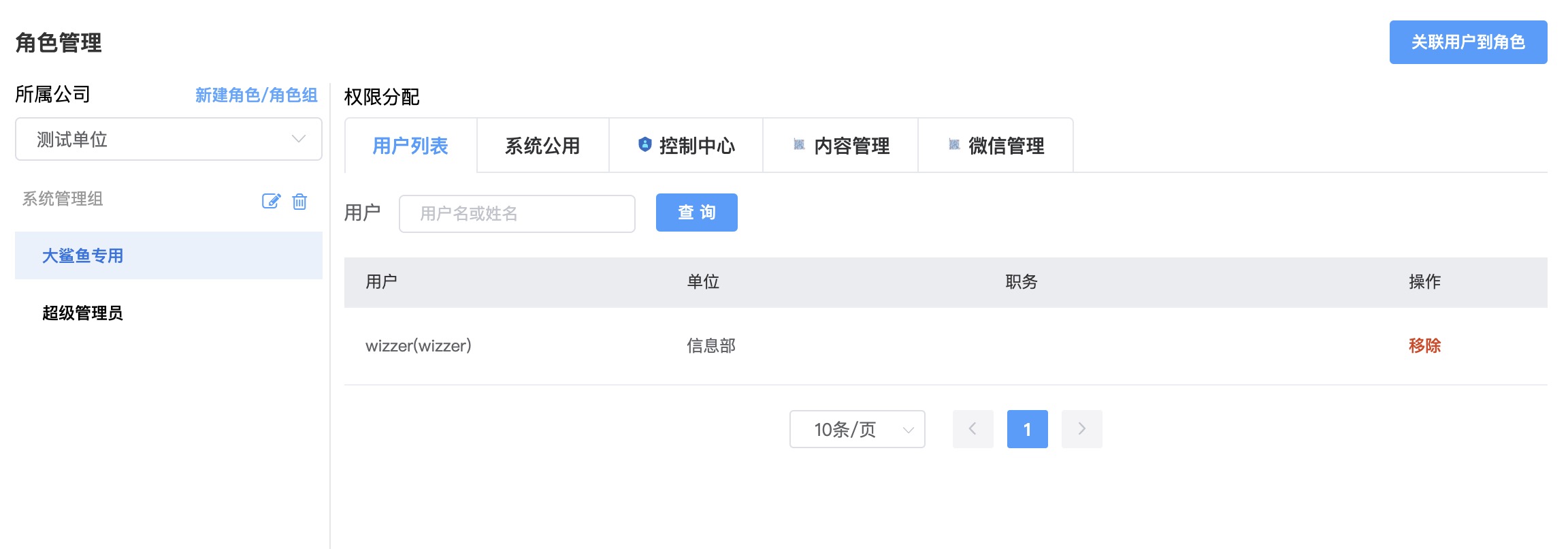
- Under the
Headquarters or Companyorganization, you can createRole GroupsandRoles, and set globally uniqueRole Codes
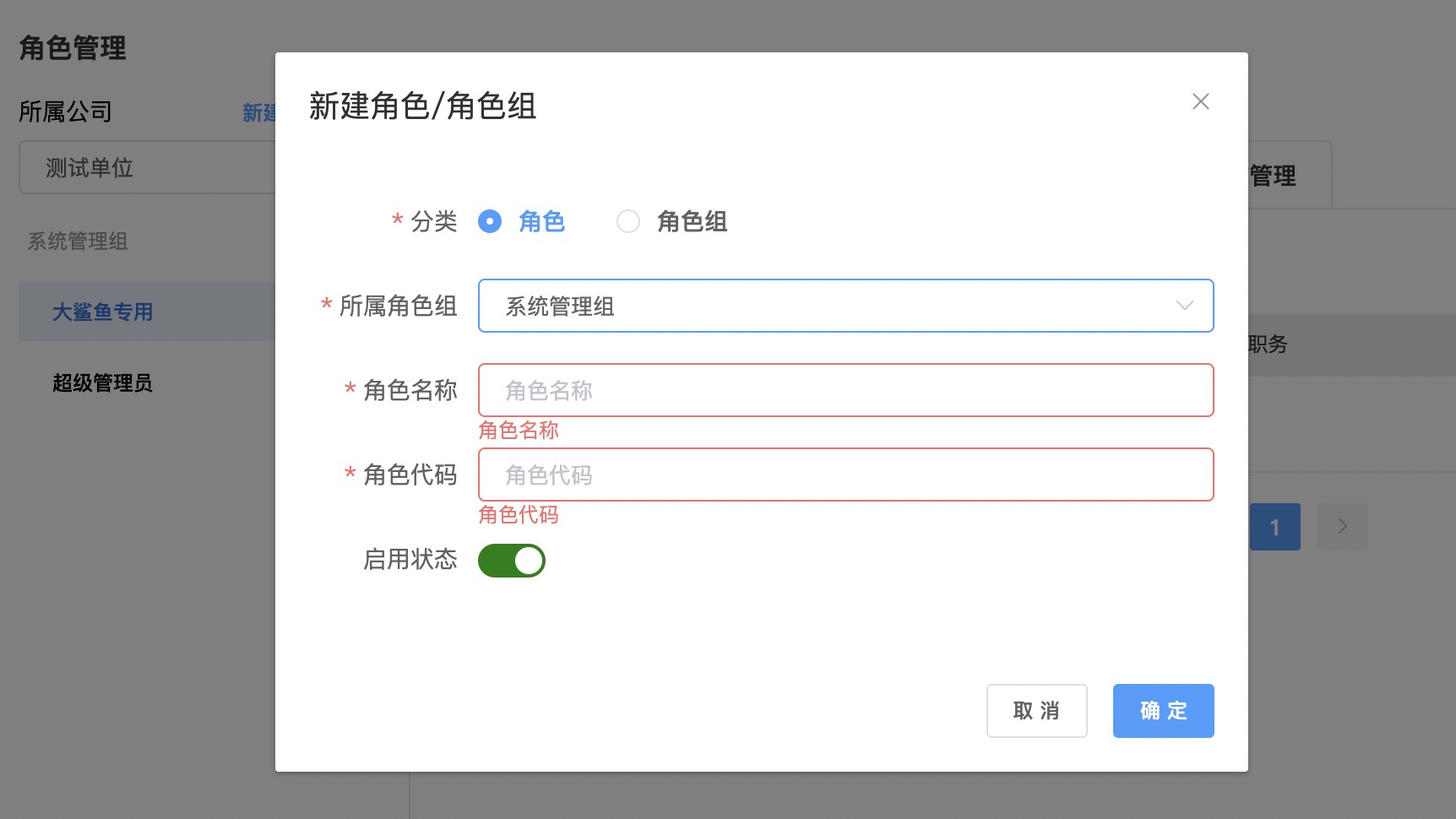
Associate Users to Roleestablishes a binding relationship betweenUsersandRoles. The relationship betweenUsersandRolesis many-to-many
- Switch to the application tab to assign
Menus and PermissionstoRolesrespectively
# Login Process
After a user enters their username and password on the login page, [Distributed Version]
wk-ucenterwill first verify the verification code. After verification passes, it will RPC call thewk-platforminterface to determine if the username and password are correctIf the username and password verification is correct, it returns the
Role CodeandPermission Identifiercollection data.sa-tokencaches theRole CodeandPermission Identifierand generates atokenwk-ucenterreturnsUser Information,Menus and Permissions,token, and other information to the frontend
# Permission Control
The backend mainly implements permission interception in the controller layer through annotations provided by
sa-token:SaCheckPermission Permission Identifier,SaCheckRole Role Code,SaCheckLogin Whether Logged InIn addition to annotations, you can also judge permissions in the code through utility class methods such as
StpUtil.checkPermission("")As an additional note, why choose
sa-tokenand abandonshiro? Because those who have suffered withshirofor a long time understand...
@At
@Ok("json")
@GET
@SaCheckPermission("sys.manage.menu")
public Result<?> data() {
NutMap map = NutMap.NEW();
map.addv("apps", sysAppService.listAll());
return Result.data(map);
}
- The frontend mainly controls whether page components are displayed through the encapsulated
v-permissiondirective
vue3
<el-button
v-permission="['sys.manage.menu.create']"
size="small"
type="primary"
@click="openAdd"
>
Create Menu
</el-button>